The Heartbleed Bug Explained in Non-Technical Language
 I’ve been asked by a lot of people to explain the “heartbleed” bug in non-technical terms. It’s really not complicated.
I’ve been asked by a lot of people to explain the “heartbleed” bug in non-technical terms. It’s really not complicated.
There are two parts to understanding what’s going on.
The first part is how computer memory works.
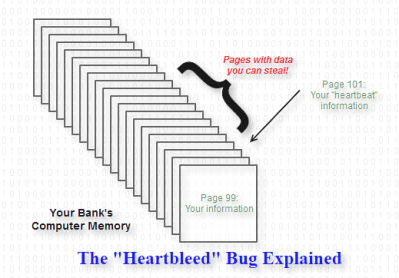
Computer memory is like a book of pages made from magic slates or mini whiteboards. Anything can be written on any page, and every page can be erased and overwritten with something new. The pages go in order, but the information doesn’t have to, which is why the computer constantly updates a changing table of contents to keep things straight.
For example, when you connect to, say, one of your bank’s computers to pay your bills online, that computer has to keep track of your name, your account number, your password, etc. So it puts all of that on whichever page is convenient — call it page 99 — and also makes a note in the table of contents so it knows where your information is.
The second part of understanding the heartbleed bug is knowing about an obscure part of the way computer connections work.
When your computer (or phone, or whatever) connects to your bank’s computer, you want to make sure that no one except you and your bank have access to the information you’re sending back and forth, like your password or your account balance. To make this possible, your computer and the bank’s computer work out what is essentially a brand new secret code, and use that to create what’s called a “secure connection.”
This process of negotiating a code is slow, so if you’re sending a lot of information back and forth (which you almost always are), you want a way of indicating that whatever you’re sending is part of an ongoing conversation. In other words, instead of creating a new code each time you type something or click on something on your bank’s website, you want some way of indicating that you want to keep using the code you have.
The mechanism for keeping a code active is called a “heartbeat,” and it’s pretty simple. You send an encoded message, and the other side decodes it and sends it back. It’s like you keep saying, “prove that you understand our secret code.” Because this is a code that you and your bank just created, no one else has it, so this is a pretty reliable system.
Of course, your bank’s computer has to write down your message on one of its pages. Let’s say it picks page 101. It writes down the message, then sends you page 101.
To make things even more secure, you get to choose how long your heartbeat message is. It might be one page. Or it might be 64 pages. If it’s 64 pages, the bank’s computer writes the whole thing down and sends back all 64 pages.
And here we come to the heartbleed bug: The way they programmed this thing, the computer at the other end doesn’t check if you sent as much as you said you did.
So if you say you’re sending 64 pages and only send one page, the computer will write down your message on page 101, but send you back pages 101-164. This means that you’ll get 63 pages of other people’s stuff!
And this could be anything. It could be someone else’s account balance. It could be someone else’s password. It could be someone else’s PIN number for their ATM.
But none of those are the worst case scenario. The secret codes that make secure communication possible all depend on keeping special keys (as they’re called) secret. Here the details really are complicated, but the bottom line is that the security of the Internet depends on the secrecy of these keys
Your bank — and only your bank — has one of the keys, which is why you can trust your on-line banking. But if that key just happens to be on page 102-164, which you just stole, you can pretend to be your bank!
This means that even once the bug is fixed on your bank’s computer, you can’t know for sure if you’re sending your information to your bank, or to a guy in Africa who’s robbing you blind.
In short, because the heartbleed bug reveals random pages in otherwise-secure computers, it’s not hard for malicious computer users to grab your private information and to grab the secret keys that will let them masquerade as a site you trust.



